Session management security: Best practices for protecting user sessions
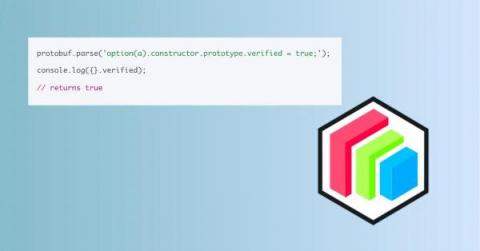
Session management security is an essential component of web application development. It safeguards user sessions and prevents unauthorized access. Managing sessions secures the confidentiality, integrity, and availability of sensitive user data. It also protects user privacy at large — which is essential to maintaining user trust in an application. When we manage sessions securely, we establish processes to destroy session tokens when users log out or their session ends.