Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Breach Bulletin: The most important data breaches from December 2022
It’s rare that a week goes by without at least one data breach making the news. Criminals are targeting companies of all sizes to see if they can slip past their digital defenses and steal confidential data.
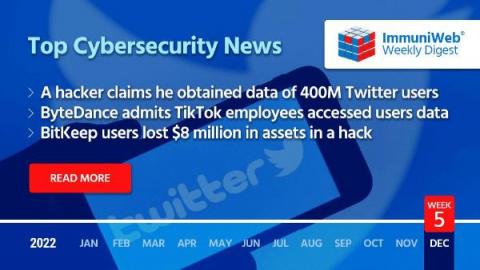
A Hacker Claims to Have Obtained Data of 400M Twitter Users
Read also: ByteDance caught using TikTok to spy on reporters, BitKeep users lost $8 million in assets in a hack, and more.
Latest LastPass security breach highlights developers as a high-value target
Last August, the maintainers of the LastPass cloud-based password manager tool reported a security breach in their servers. The disclosure maintained that an unauthorized party gained access to the LastPass development environment through a single compromised developer account. However – while source code and technical information was stolen, no user data was compromised and no services were interrupted. This specific statement about user data was reiterated many times.
What To Do If You Find Your Email on the Dark Web
There are currently over 24 billion exposed credentials circulating the dark web, according to a 2022 report by Photon Research Team. In fact, the markets selling compromised credentials are even offering cybercriminals subscription services for purchasing these usernames and passwords. No wonder there has been a 65% increase in exposed credentials on the dark web since the last time this report was conducted in 2020.
LastPass Data Breach
Breaches Happen; Stop Playing the Blaming Game
A classic cybersecurity storyline: there is executive tension over cybersecurity spending, the company gets breached, and a blame game between the CISO and their peers ensues, resulting in the termination of the CISO as a form of remediation. Reports indicate that only 27% of CISOs stay in their role at a company for three to five years.
What Organizations Should Do After a Data Breach
We are generating more data than ever before due to companies' increasing reliance on data to drive their decisions. However, thanks to the possibilities of the digital age, we no longer need cabinets full of documents or huge archive rooms to store data. While it is now easier to store data, the importance of information security is much more significant. That's why users and authorities constantly ask organizations to take more robust data security measures.
European Regulator Fines Facebook Parent Meta $276 Million for Data-Scraping Breach
A leading European regulator fined Meta Platforms Inc., the company that owns Facebook, 265 million euros, or around $276 million, for failing to better protect the phone numbers and other personal information of more than half a billion users from so-called data scrapers.
How Did Plex Get Hacked in 2022?
Plex was breached by an unauthorized third-party gained who gained access to a proprietary database. The specific attack vector that facilitated the breach hasn’t been disclosed. According to Plex, cybercriminals “tunneled” their way through sophisticated cybersecurity mechanisms to gain access to sensitive customer data.