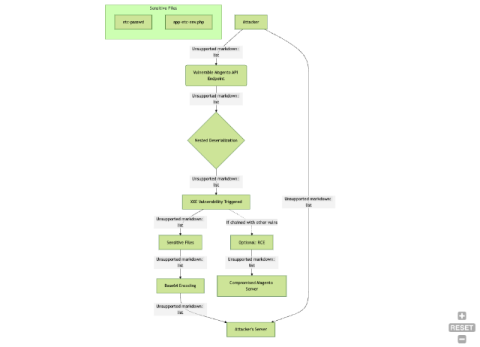
Why a solid DevOps foundation is vital for effective DevSecOps
As DevOps adoption has grown, organizations are pushing code into production faster than ever. However, the fast pace of DevOps has led many developers to view security as a bottleneck or afterthought, which means security teams need a new approach to keep up.