Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
October 2022
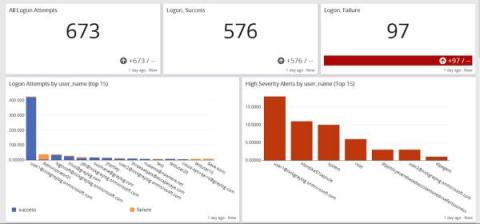
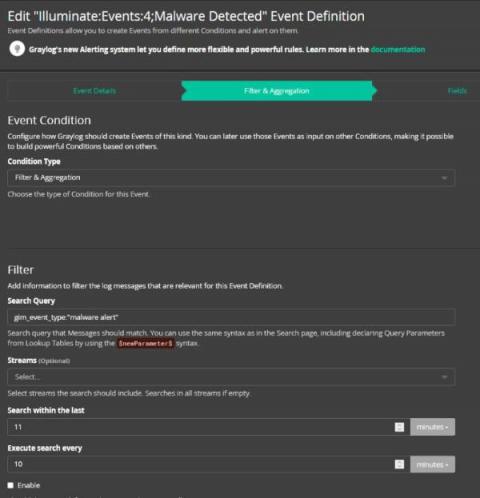
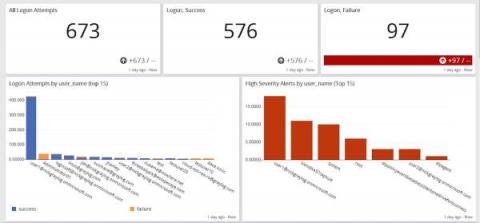
Centralized Log Management for Incident Response
Leading financial institutions hedge risk by focusing on these 5 critical SIEM requirements
Six SIEM Essentials for Successful SOCs
A few weeks ago, Gartner named Splunk Enterprise Security a Leader in the 2022 Gartner® Magic Quadrant™ for SIEM. This is the ninth consecutive year that Splunk has been placed in the Leader’s quadrant. We’re honored to be recognized and we believe our placement is a testament to our commitment to delivering a data-centric security analytics solution that accelerates threat detection and investigations.
What do telecom security teams need from a SIEM?
Top 3 SIEM challenges in multi-cloud environments
Trustwave Launches Enhanced Co-Managed SOC Capabilities to Help Clients Maximize SIEM Value and Productivity
Trustwave's Co-Managed SOC (Security Operations Center) is a powerful offering that has a tremendous track record of helping organizations maximize the value realized from their SIEM (Security Information and Event Management) investment, reducing alert noise by up to 90%, while maintaining a position of “your SIEM, your content.” The service has just received a major enhancement with the addition of Trustwave’s one-of-a-kind cybersecurity collaboration platform, Security Colony, whic
Public sector security: 4 considerations for implementing a modern SIEM
Log Management Strategy for Cybersecurity Maturity
The people have spoken and Splunk wins twice at the ITAwards
You know that us Splunkers love to go deep into use cases and figure out what helps our customers the most. However in today’s business world, industry recognition goes a long way in proving the value in the products and services we use. For example if you were Munich Airport, then it would speak volumes to others if your airport was named as a “First Five-Star Airport” or if you were Dachser Logistics and went on to win the “One Eaton Supplier Premier Award”.
ManageEngine recognized in the Gartner Magic Quadrant for Security Information and Event Management for the sixth time!
Today, we’re excited to announce that ManageEngine has been recognized in the 2022 Gartner Magic Quadrant for Security Information and Event Management (SIEM), appearing in the report for the sixth time in a row. We are thrilled to be awarded this recognition yet again for our contribution in the SIEM landscape. Get a complimentary copy of Gartner’s latest Magic Quadrant for SIEM here. The shift to cloud computing has accelerated in the last two years.
Sneak Peek: Elastic's 2022 Global Threat Report
Micro Lesson: Security Automation with Cloud SOAR Playbooks
Do You Know Who's in Your Cloud? Preventing Identity-Based Threats with CIEM
As organizations continue to shift to multi-cloud environments and increasingly use cloud services for application development, new challenges emerge that require dramatic changes in the delivery and practice of cybersecurity.
New SOC Performance Report: Security Analysts Are Overworked and Under Resourced
The fourth annual Devo SOC Performance ReportTM shows security professionals believe the SOC is significant to their organization’s cybersecurity strategy. As noted in our last blog, 77% of respondents say their SOC is “very important” or “essential” to their organization. But there’s pain behind the scenes as well. The report notes the majority of security professionals are feeling overwhelmed due to too much work and not enough resources.
Maturing Your Security Hygiene
2Torial: Protect All of Your Endpoints with Elastic Security
Convince Your Boss You Need These Managed IT Security Services
Considering managed it security services? It is more important than ever to have a resilient security posture. Hackers are constantly looking for ways to exploit weaknesses in systems, and even a small data breach can have devastating consequences.
Elastic continues to gain momentum in SIEM market
2022 Gartner Magic Quadrant for SIEM: Sumo Logic positioned as a Visionary for the second year in a row
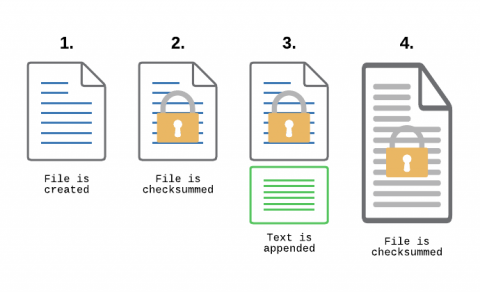
Monitoring Transaction Log Files for PCI compliance
File Integrity Monitoring, aka as FIM, is a must-have feature for anyone in charge of security. With FIM, one can detect when a critical file, such as a file that belongs to the Operating System, or a key configuration file, is changed. In most cases, configuring FIM is straightforward: If the file changes then generate an alert.
Datadog alternatives for cloud security and application monitoring
2022 Devo SOC Performance Report: Familiar Challenges Facing Security Workers
The fourth annual Devo SOC Performance ReportTM shows that issues facing organizations since the start of the global pandemic in early 2020 continue to affect SOC performance, including challenges in hiring and retaining SOC talent. Based on the independent survey of more than 1,000 global cybersecurity professionals commissioned by Devo and conducted in the Summer of 2022, the report examines current SOC trends and challenges. The good news?
7 key features of SIEM that every enterprise administrator should be aware of
A SIEM solution has become an integral part of an organization’s security arsenal. But organizations often overlook the system’s capabilities, owing to a belief that SIEM functionalities are too complex and the architecture inscrutable. Regrettably, they neglect to meet the requirements of their organization with the features of the product. For instance, an organization that deals with the credit card information of customers needs to comply with the PCI-DSS requirement.
Cyber Hygiene with Centralized Log Management
Elastic Wins 2022 CyberSecurity Breakthrough Award for Threat Intelligence Platform of the Year
Extract maximum value from your Microsoft Sentinel SIEM with Sysdig Secure
Sysdig has validated its security, monitoring, and compliance capabilities with multiple Azure-related services. The latest is Microsoft Sentinel, a SIEM(Security Information and Event Management) solution on Azure that works really well with Sysdig’s cloud workload protection capabilities. Sysdig and Microsoft have a common goal of helping customers ship cloud apps faster by helping them see more, secure more, and save time in troubleshooting deployed microservices.