Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
June 2021
Tokens, TLS and Teleport
How Cloud Evangelists Face - and Overcome - Cloud-Computing Security Challenges
This is the third in a series of posts examining the recent Devo research report, Beyond Cloud Adoption: How to Embrace the Cloud for Security and Business Benefits, which is based on a survey conducted by Enterprise Strategy Group (ESG). This time, we’ll take a look at the cloud-computing security challenges Cloud Evangelists face. Let’s begin by explaining how we define that group.
Not Laughing: Malicious Office Documents using LoLBins
Attackers have long used phishing emails with malicious Microsoft Office documents, often hosted in popular cloud apps like Box and Amazon S3 to increase the chances of a successful lure. The techniques being used with Office documents are continuing to evolve. In August – September of 2020, we analyzed samples that used advanced techniques like: In January 2021, we examined samples that use obfuscation and embedded XSL scripts to download payloads.
Why companies need URL filtering for enhanced cloud protection
The cloud landscape is rife with unsafe URLs and inappropriate content. This—coupled with the accelerated adoption of cloud applications in the workplace—has created an urgent need to scrutinize and control the use of these online resources to prevent data theft, exposure, and loss. This blog elaborates on how a robust URL filtering solution can help manage what cloud services your employees use and how they interact with these services.
Securing DevOps : Security in the Cloud
Netskope CTE and CrowdStrike Demo
The Right Steps to SASE: Refactor Internal Data Center Controls to Closed Loop Risk Management
The following is an excerpt from Netskope’s recent book Designing a SASE Architecture for Dummies. This is the sixth in a series of seven posts detailing a set of incremental steps for implementing a well-functioning SASE architecture. Throughout this series, we repeat that the data center is just one more place people and data have to go—it’s no longer the center of attention.
Is Google Drive HIPAA Compliant?
Google Drive is one of the oldest and most well known cloud storage and productivity suites. Although Google Drive launched in 2012, Google’s productivity platform dates back to 2006, when Google Docs and Google Sheets first launched. Over the years, Google would more closely integrate these services before moving them under the Google Drive and Google Suite brand. Today, Google Drive and Google’s entire suite of collaborative tools are referred to as Google Workspace.
Cloud Computing Security: A Primer
Gartner forecasts that worldwide public cloud end-user spending will grow 23% to USD 332.3 billion in 2021 as cloud technologies become mainstream. As cloud computing architectures continue to become more prevalent, “cloud native” has become a popular buzzword. But what exactly does “cloud native” mean and what impact does it have on security? How exactly do you secure all these cloud native applications?
Tagging Teleport Resources with Labels
5 Top Tips for Cloud Security from Enterprise CISOs
The Financial Times hosted an excellent event recently, at which I joined Naina Bhattacharya, CISO for Danone; Manish Chandela, Group CISO for Unipart and Florence Mottay, Global CISO for Ahold Delhaize, to discuss cloud security. The FT’s Dan Thomas moderated and the panellists all shared some excellent and candid insights into cloud threats and security strategies within their organisations.
Cloud Threats Memo: Beware of Leaky Buckets and Cloud Apps
Another memo, another leaky cloud app compromising the personal information of hundreds of thousands of individuals (and yes, you can easily guess the app that exposed the data so no spoiler alert needed—it was an S3 bucket). The latest organization to join the long list of victims of cloud misconfigurations is Cosmolog Kozmetik, a popular Turkish online retailer that exposed more than 9,500 files, totaling nearly 20 GB of data.
Teleport has been named a Cool Vendor in Gartner's Identity-First Security report
Today we are happy to announce that Teleport has been included as a Cool Vendor in Gartner Cool Vendors in Identity-First Security report. “We believe Teleport’s inclusion in the Identity-First Security Report by Gartner is confirmation that Teleport solves a huge problem of accessing cloud-native resources that traditional PAM tools did not,” said Ev Kontsevoy, co-founder and CEO of Teleport.
Trends in Cloud Adoption: Why Cloud Computing is on the Rise
In this post, I’ll answer one question: Have we reached the tipping point for cloud proliferation? According to the report, the answer is yes. ESG surveyed 500 IT and security professionals working in the security operations center (SOC) chain of command at organizations with more than 1,000 employees in North America and Western Europe in Q1 of this year.
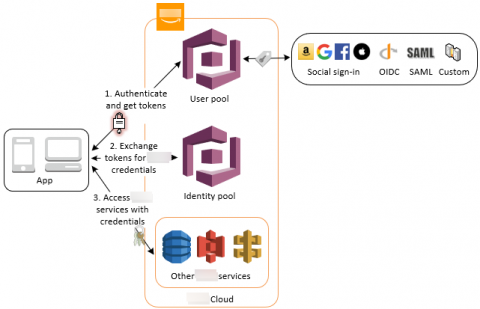
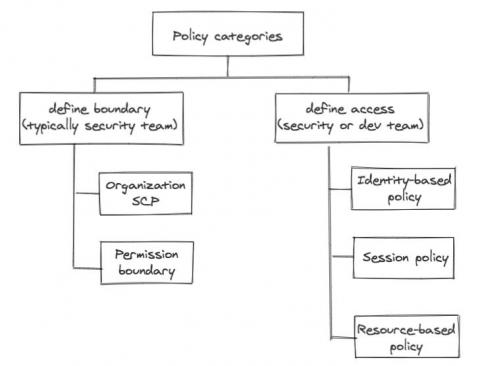
How does AWS IAM role, STS and Identity Pool work with each other.
We talked about IAM in the past 3 posts, identities in IAM, manage users privilege as an IT person and control privilege boundaries. We also talked about how applications use AWS Cognito Identity Pool to get AWS temporary credentials to access AWS resources in early posts of “What I wish I could have learned before starting using AWS Cognito” and “Authentication and authorization with AWS Amplify under the hood”.
Amazon RDS Restore Guide
The SASE Solution to Network and Security's Complicated Relationship Status
If our friends Security and Networking were on Facebook, they would probably both list their relationship status as “It’s Complicated.” Sometimes everything’s great, but now and then things can get a little weird, unclear, or uncomfortable. At many organizations, there has traditionally been a barrier between the security and networking teams. Each team has its own objectives — and at times, those objectives can be at cross-purposes.
Detecting and Investigating Threats in Splunk Security Analytics for AWS
The Top 5 Vendor-Neutral Cloud Security Certifications of 2021
Most organizations have already begun their shift to the cloud. In its Cloud Computing Survey 2020, for instance, International Data Group (IDG) found that 81% of respondents had at least one workload or segment of their computing infrastructure in the cloud. That percentage could grow by the end of the year, as IDG found that 32% of total IT budgets will go to cloud computing—up from 30% in 2018.
Introducing the World's First Modern Cloud-Based SecOps Platform: Splunk Security Cloud
To say that the past year presented its fair share of cybersecurity challenges to the InfoSec community would be a drastic understatement. The rapid migration to remote work at scale left 80% of CIOs unprepared, and SecOps teams struggled to confront the evolving threat landscape with disparate toolkits and skill sets. Not to mention that as more organizations shifted to hybrid and multi-cloud environments at scale, cloud complexity (and cloud-based threats) skyrocketed.
Snyk Container is now an extension in the AWS CloudFormation Registry
Snyk is excited to announce the general availability of Snyk Container as an officially supported and published extension in the AWS CloudFormation Registry! The CloudFormation Registry lets you manage the extensions that are available for use in your CloudFormation account. Public third-party extensions, like Snyk Container, are made available in the registry for use by all CloudFormation users alongside those published by Amazon and must be activated before use on your account.
Top 5 Security Risks of Cloud Computing
Many businesses are shifting workloads to the cloud in an effort to increase efficiency and streamline workloads. In fact, according to the Flexera 2021 State of the Cloud Report, roughly 90% of enterprises anticipate cloud usage will expand even further as a result of COVID-19. While cloud computing can offer organizations a competitive advantage, it is important not to rush into cloud adoptions without understanding the risks involved as well.
Sharing SSH Sessions with Teleport
Lookout Announces Expanded Partnership with Google Cloud to Deliver Zero Trust Security from Endpoint to Cloud
Cloud-based solutions have become essential to how we work and play in the digital era. Many organizations continue their rapid embrace of cloud-based solutions to enable their employees the flexibility to work from anywhere. Cloud spending this year could hit $332 billion, up 23% from 2020, according to a forecast by Gartner, Inc. 1 The cloud has raised our expectations regarding productivity as organizations view the cloud as a true engine of competitive advantage.
JFrog CloudFormation Modules Make Provisioning to AWS Easy and Secure
A routine cloud operations task should have a routine solution. That’s why we’ve just made it a lot easier to install and maintain self-hosted instances of the JFrog DevOps Platform on AWS, through AWS CloudFormation. To further simplify the effort of self-hosting Artifactory and Xray on AWS, we’ve just published a set of AWS CloudFormation modules to the AWS CloudFormation Public Registry.
Scan for AWS CloudFormation misconfigurations with Snyk IaC
We’re excited to announce the launch support for AWS CloudFormation in Snyk Infrastructure as Code. In our recent Infrastructure as Code Security Insights report, we found that 36% of survey participants were using AWS CloudFormation (CF) as their primary infrastructure as code tool of choice. Using Snyk Infrastructure as Code, you can now scan your CF YAML or JSON templates against our comprehensive set of AWS security rules.
Cloud Threats Memo: Illustrating Big Risks in the Shift to Remote Working
The exploitation of traditional remote access technologies is reaching new records. That, in a nutshell, is the main finding of Nuspire’s Threat Landscape Report Q1 2021. The report, sourced from 90 billion traffic logs during Q1 2021, looks at a range of events such as malware activity, botnet activity, exploitation activity, and remote access. The remote access section probably best illustrates the risks posed by the sudden shift to remote working.
Bridging the Network-Security Divide with SASE Thinking
The many business benefits made possible by digital transformation are undoubtedly making waves across industries. Data is the raw material that drives smarter decision-making, and as such, drives value for organizations, but things quickly get challenging when you start to consider how all that data will be used—and who has access to it, when.
The Right Steps to SASE: Extend Zero Trust to Data Protection and Private Access
The following is an excerpt from Netskope’s recent book Designing a SASE Architecture for Dummies. This is the fifth in a series of seven posts detailing a set of incremental steps for implementing a well-functioning SASE architecture. Now that your organization is smarter about its traffic, able to see what’s going on, and able to enforce policies to secure its data, you can realize the promise of a remote-first workforce.
AWS IAM in a layman's terms
We alluded in one of our previous posts that the development team will own a lot of responsibility defining application related resource access control, simply because the dev team owns the infrastructure as code (IaC) responsibility themselves. No matter how security-savvy and security-educated a development team is, the central security team still needs some control, some kind of “trust but verify”.
Netskope Named a 2021 Gartner Peer Insights Customers' Choice for Secure Web Gateway
At Netskope, one of our core values as a company is that customers are always our number one priority. We know that technology projects are rarely easy undertakings and it’s our job to be there for our customers and for them to know we have their backs. With that in mind, we are excited to announce that Netskope has been recognized as a Customers’ Choice in the June 2021 Gartner Peer Insights ‘Voice of the Customer’: Secure Web Gateway.
Who Do You Trust? OAuth Client Application Trends
Federated identity systems, such as Google Identity, bring security and convenience in the form of SSO for Internet or cloud applications. It is common to be prompted for authentication in order to grant various levels of access or permissions for applications ranging from Google Drive, Google Cloud SDK, Google Chrome plugins, Slack, Adobe, Dropbox, or Atlassian to numerous third-party apps.
Cloud Threats Memo: Takeaways From the Q1 2021 Phishing Activity Trend Report
The Anti-Phishing Working Group (APWG) has just released its Phishing Activity Trend Report for Q1 2021. The first findings are easily predictable; the dispersion of the workforce is pushing phishing attacks to new records: just in January 2021, the APWG detected 245,771 unique phishing sites, the highest number reported so far.
Bad guys are watching for new openings in your cloud, are you?
You see the headlines, and perhaps, ‘thank goodness it wasn’t us’ flickers through your mind. An overly permissive web server exposes 100 million+ consumer credit applications, or an S3 bucket leaves hundreds of millions of user records open to the public. A nightmare scenario for any CISO and their cloud security team!
Five worthy reads: Confidential computing - The way forward in cloud security
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. In light of rising concerns over cloud cybersecurity, this week we explore the concept of confidential computing. The past year has seen strong adoption of cloud technologies due to accelerated digital transformation and a cloud-first approach in business.
Is Atlassian Cloud HIPAA Compliant?
In 2021, digital transformation has accelerated. At the tail end of the COVID pandemic, with companies remaining remote, the demand for cloud services in the enterprise is the highest It’s ever been. Healthcare organizations, which more directly encountered the acute challenges posed by the pandemic, were among the first to be shaped by the current wave of digital transformation.
The Right Steps to SASE: Introduce Zero Trust Principles to Web, Cloud, and Activity Access
The following is an excerpt from Netskope’s recent book Designing a SASE Architecture for Dummies. This is the fourth in a series of seven posts detailing a set of incremental steps for implementing a well-functioning SASE architecture. This is when you’ll begin to put NG-SWG to work as you lay the foundation of your SASE. Fortunately, the capabilities needed to set things right are built into NG-SWG.
Not All CASBs Are Created Equal. How Do You Choose?
Software as a service (SaaS) apps have reshaped the way we stay productive. By having everything easily accessible in the cloud, we are able to get work done from anywhere and on any device. But, as we know, this flexibility has also introduced security challenges, as your data is also easier to reach for malicious actors. This is why the purchase of a cloud access security broker (CASB) is never that controversial. Most organizations understand that cloud apps require additional protection.
Key Considerations for the Future of Work
In summer 2020, as it became abundantly clear that remote working in response to the COVID-19 pandemic was here to stay, Netskope surveyed more than 400 end-users in the US from across many industries, including telecommunications, IT, government healthcare, finance, nonprofit, and education, about their thoughts related to remote working.
5 Tips and Tricks for Cloud Native Security
Cloud-native applications that are based on new types of infrastructure such as containers and serverless platforms are being rapidly adopted by organizations worldwide. While cloud-native applications deliver compelling benefits such as elastic scalability, unmatched resilience and rapid development velocity, they also raise challenges.
Snyk Builds Security into AWS CodePipeline to Mitigate Open Source Risk for Developer and Security Teams
Ensure Cloud Security With These Key Metrics
Operationalizing IP Allow Lists for Cloud Environments
If applying IP allow lists to the cloud excites you as much Another One Bites the Dust on volume 11, read on. In this blog, I’ll discuss some considerations regarding operationalizing, automating, and increasing the efficacy of IP allow lists in your cloud infrastructure. Although this discussion will be in the context of cloud infrastructure providers such as AWS, GCP, and Azure, it should also be applicable to other cloud infrastructure and application environments.
Cloud Threats Memo: RDP Misconfigurations and Initial Access Brokers
A recent study by Sophos has added more fuel to the RDP fire, confirming that the exploitation of this service, when not adequately protected, remains one of the preferred techniques to compromise an organization. Not only has the exposure of RDP servers, driven by the pandemic, led to an exponential increase of brute-force attacks against this service, but it has also encouraged a flourishing market of initial access brokers.
Cloud Security Architecture: 5 Best Practices
Cloud programs like Slack and Google Drive allow businesses to work collaboratively and efficiently, often at a low cost. However, these cloud platforms open a business up to new levels of risk: sharing information via cloud programs can put customer data at risk. Cloud security architecture provides a way to recognize and remedy vulnerabilities that result from using cloud service providers (CSPs).
A Team-Centric View of Security with Snyk and CloudBees
A Real-World Look at AWS Best Practices: Password Policies
Best practices for securing an AWS environment have been well-documented and generally accepted, such as AWS’s guidance. However, organizations may still find it challenging on how to begin applying this guidance to their specific environments. In this blog series, we’ll analyze anonymized data from Netskope customers that include security settings of 650,000 entities from 1,143 AWS accounts across several hundred organizations.
The Right Steps to SASE: Place Core Inspection Points Between Users and Apps
This is the third in a series of seven posts detailing a set of incremental steps for implementing a well-functioning SASE architecture. With a Next Generation Secure Web Gateway (NG-SWG) firmly in place and your visibility into all your traffic dramatically increased, one thing is certain: You may not like what you see next. Are your people using Microsoft Office 365? Salesforce? Workday? Box? The answer is almost certainly, yes.
Egnyte Expands Content Governance and Compliance Solutions for Google Workspace and Dropbox
If you’re like most companies, your teams rely on a variety of cloud apps and storage solutions to get work done and collaborate with internal and external teams. While this flexibility is great for end users, it creates enormous complexity when it comes to data security and governance. IT teams must juggle multiple administrative dashboards, permissions configurations and access control policies across apps.
Meet The Authors - Cloud Services
Overcoming Compliance Issues in Cloud Computing
The benefits of organizations moving some or all their IT workloads to the cloud are well-known and numerous. There are several challenges to successful cloud adoption, though, and one of the most important of them is compliance. Whether your cloud use case is low-cost data storage, scaling your infrastructure for critical business apps or disaster recovery, this article helps inform you about and overcome compliance issues in cloud computing.
How secure use of the cloud can digitally transform your business
Companies that move towards digital transformation can innovate more quickly, scale efficiently and reduce risk by implementing cloud security best practices. Businesses must keep up with growing customer expectations and the pace of innovation by adopting a digital-first business model. But for many businesses, digital transformation remains a huge challenge. Company culture and technology must align for a digital-first business model to be effective.
Introducing Sumo Logic Cloud SIEM powered by AWS
3 Key Observations on Network and Security Transformation
Recently I attended another great Evanta CIO event, and in the course of a day packed with excellent talks and knowledge-sharing opportunities, I had the opportunity to sit down and discuss the topic of network and security transformation with Stuart Hughes, the CIDO at Rolls Royce. Stuart shared his experiences over the past 18 months, discussing how the pandemic—among other things—had changed his strategic approach to security.
Understanding the Cloud Security Challenges for SMBs
The events of 2020 didn’t prevent small- to mid-sized businesses (SMBs) from adopting the cloud. Impact Networking reported that SMBs’ overall cloud spending grew 6.3% between 2019 and 2020. Such growth is projected to lead more than a third (35%) of SMBs to annually spend between $600,000 and $1.2 million on public cloud services by the end of 2021, noted Statista.