Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
September 2020
Dangerous Docs: Surge in Cloud-delivered Malicious Office Documents
The global pandemic caused an abrupt shift to remote work among enterprise knowledge workers, which in turn resulted in an increase in risky behavior. Attackers immediately tried to capitalize on the pandemic, with COVID-19-themed phishing emails, scams, and Trojans. At the same time, techniques used in more sophisticated cyberattacks continued to evolve.
Sysdig Boosts AWS Security with the First Automated Inline Scanning for Fargate
Fargate scanning in under 4 minutes
Leaky Images: Accidental Exposure and Malware in Google Photos and Hangouts
Did you know that the default link sharing option in Google Photos allows anyone with the link to view the files and all images shared in Google Hangouts that are publicly accessible? In this edition of our leaky app series, we will cover how image link sharing in Google Hangouts and Google Photos can lead to the accidental public exposure of sensitive data. We will also look at the threat detection capabilities of Google Photos and Google Hangouts.
Stories from the SOC - Cloud and On-site Protection
One of the benefits of having your managed detection and response (MDR) service managed by AT&T Cybersecurity is the visibility into threats from a large number of customers of all sizes and across different industries. This allows the team to take what they learn from one customer and apply it to another. Our security operation center (SOC) analysts were able to use an OTX alarm and an AWS correlation rule to discover open ports on public facing servers for two different customers in 24 hours.
iDevNews Application Architecture Summit 2020 | RBAC for SSH and Kubernetes Access with Teleport
Demo | Access Workflow Integration Using Pager Duty | Privileged Access Management | Teleport
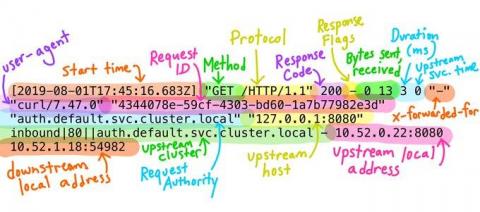
Leveraging logs to better secure cloud-native applications
Escape The Ticketing Turmoil | Slack/PagerDuty Integrations | Teleport Workflow API
Why Your Org Needs DLP for Slack: Ensuring Long-Term Data Security
Cloud security requires long-term investments to get right. Today’s demands of remote work and collaboration across teams are forcing security leaders to make fast decisions about which business tools they should allow their orgs to adopt. Data loss prevention (DLP) is a good way to support cybersecurity policies that will safeguard sensitive data and perform at the highest levels of security over the long haul.
SKILup Day DevSecOps | How To Securely Access Compute Resources In Cloud Environments | Virag Mody
Cloud security series: What is cloud security?
Cloud security is the implementation of security controls to protect confidential information stored in cloud environments and reduce the risk of data breaches. Effective cloud security involves regularly assessing and hardening defences, ensuring broad threat visibility and rapidly responding to threats.
Hybrid Cloud Security
Hybrid cloud is an increasingly popular infrastructure option for companies in industries from game development to finance. But what is it, and what are the most effective hybrid cloud security practices for protecting your sensitive and regulated data?
SaaS Security: All Questions Answered
Secure and monitor AWS Outposts and hybrid clouds
Today we announced that Sysdig has demonstrated successful integration of our monitoring and security software with AWS Outposts and achieved the AWS Outposts Ready designation. AWS Outposts provides a fully managed service that extends AWS infrastructure, services, APIs, and tools to your datacenter, co-location space or “edge” location to support on-prem and hybrid cloud use cases. AWS Outposts provides a hardware and software stack built on Amazon’s EC2 public cloud expertise.
Netskope NewEdge
Netskope Threat Coverage: Emotet
Emotet is one of the world’s prolific modular botnets that has several evasive and technical variations up its sleeve. After a brief intermission, Emotet has recently re-emerged using massive malspam campaigns.
Webinar | Industry Best Practices for SSH Access | Teleport | How To
Risky Business: How COVID-19 changed user behavior
The COVID-19 pandemic caused an abrupt change — a sudden and lasting shift to remote work for the majority of knowledge workers. The number of people working remotely more than doubled in the span of a few weeks. Among the many challenges that security organizations faced during this transition was a change in user behavior.
Best Practices for Secure Infrastructure Access
Technologies build on other technologies to compound growth. It’s no coincidence that of the companies with the highest market capitalization within the US, the first non-tech company is the eighth one down: Berkshire Hathaway. Nor is it a coincidence that tech startups can take their valuation into the 10 digits in a flash on the backs of other tech companies. This pace of growth can only be afforded by the innovation of new technology.
Leaving Bastion Hosts Behind Part 3: Azure
This post is the third in a series about alternatives to bastion hosts in each of the major cloud providers. The first post covered an introduction to bastion hosts, the SSH multiplexing attack, some disadvantages to managing your own bastions, and an alternative solution in GCP. The second post covered the Session Manager service provided by AWS.
Cloud Challenges by the Numbers: Adoption and Configuration
The year 2020 has shown us that cloud computing is among the most powerful capabilities humanity has, enabling people around the globe continue their everyday business and education uninterrupted. We continue gathering the most interesting findings from industry research. If you’re interested in learning statistics on cloud usage, top cloud initiatives and cloud security concerns, read the 2020 State of the Cloud Security Statistics article.
Top 6 Security Threats in Cloud Computing and How to Mitigate Them
In this digital era, more companies are encouraging or requiring employees to work from home. In addition to allowing employees to access the corporate network using their own devices, they are also turning to cloud computing, which is cost-effective and scales easily. However, not all of these organizations are prepared for the associated cloud security threats. Cloud providers often offer some protection capabilities, but their responsibility is primarily to ensure service availability.
Why Network Peering & Interconnections Matter
In previous blogs on the Netskope NewEdge network, we’ve discussed concepts including Secure Access Service Edge (SASE) architecture and why counting data centers alone is meaningless when trying to understand cloud service coverage. Now that we’ve laid the foundation it seems like a good time to get into what’s needed in terms of architecting the actual network and the connections required.
Webinar | How Decisiv Scaled Global Remote SSH Access and Remained Compliant With Teleport
Mitigating the Risks of Instance Metadata in AWS EKS
Compromising a pod in a Kubernetes cluster can have disastrous consequences on resources in an AWS Elastic Kubernetes Service (EKS) account if access to the Instance Metadata service is not explicitly blocked. The Instance Metadata service is an AWS API listening on a link-local IP address. Only accessible from EC2 instances, it enables the retrieval of metadata that is used to configure or manage an instance.
Migrating from On-prem Proxies to the Cloud
Recently, a Fortune 500 customer asked us to migrate 5 million lines of URL policies into our cloud solution. This configuration included frequently used websites like Office.com, Linkedin.com, and Box.com as well as hundreds of other URLs and domains that were no longer reachable or registered anymore. Our first question to the customer was, “Help us understand why you would want to do that?”, in the context of migrating their entire configuration.