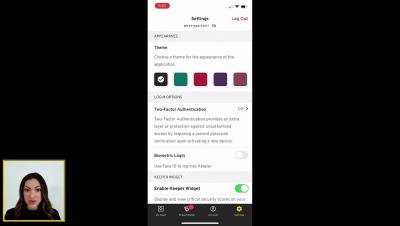
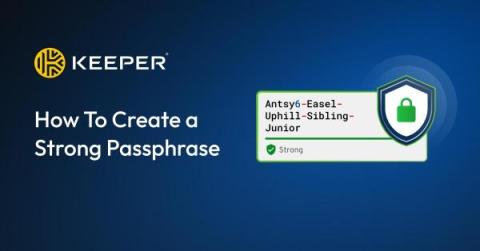
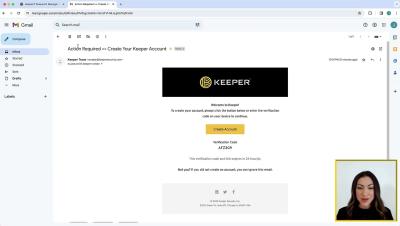
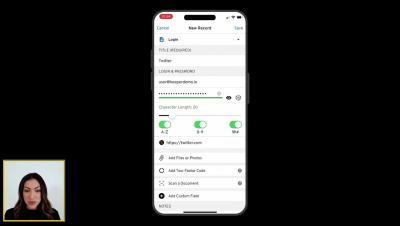
Keeper 101 - How to Create Your Keeper Account on Android
Learn how to create your Keeper Account on iOS in less than 2 minutes with our step-by-step guide. Signing up for Keeper's Android mobile app is easy. Simply visit the Google Play Store on your device, search for Keeper, and install the Keeper Password Manager application. Once the download is complete, tap Open to start Keeper.