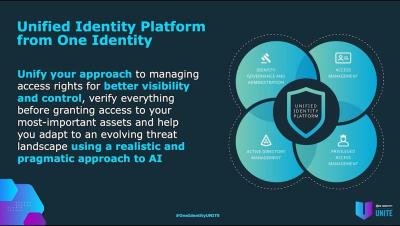
Is Your Company's Website Compromising Customer Data?
If you are a security, compliance, and privacy professional, it’s time to focus on an often-ignored issue—client-side security. While many organizations dedicate significant resources to protecting their servers, there’s a critical question to consider: are you also safeguarding what’s happening on your users’ browsers?