The 2024 Open Source Security and Risk Analysis (OSSRA) Report | Synopsys
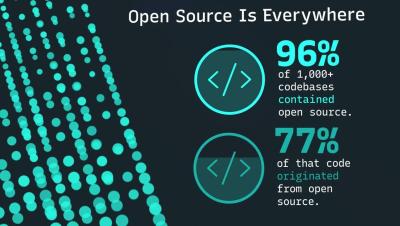
Open source is in everything, everywhere, all at once. Get an in-depth look at the current state of open source security with the ninth edition of the “Open Source Security and Risk Analysis”(OSSRA) report. Do you know what's in your code?