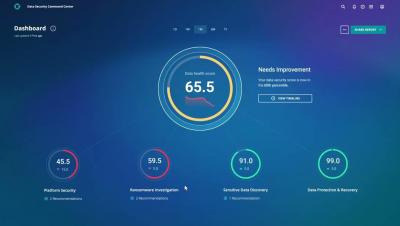
How to Streamline Security Operations With Identity Security Intelligence
“Black Swan” author Nicholas Nassim Taleb once wrote that “intelligence consists in ignoring things that are irrelevant (avoiding false patterns).” Organizations must take this definition to heart as they incorporate Identity Security intelligence – an essential element of any Zero Trust cybersecurity strategy. Many organizations have dedicated Security Operations Center (SOC) teams responsible for their threat detection, investigation and response efforts.