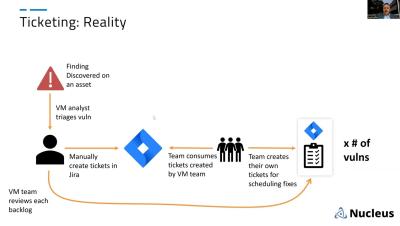
What Does a Solid VM Ticketing Workflow Actually Look Like?
In this webinar, Scott Kuffer discusses the challenges and best practices of vulnerability management workflows and ticketing. He emphasizes the discrepancy between vulnerability management teams' priorities and the priorities of the business as a whole. Scott explores different ticketing workflows, starting with basic vulnerability-based tickets and progressing to more advanced options such as asset-based, team-based, and action-based tickets. He highlights the benefits of automating ticket creation and reporting, as well as the potential for redefining how vulnerability management is approached within organizations.