Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Vulnerability
Dev First Prevention Strategies Using the CI/CD
Zero Day Defined: Zero-Day Vulnerabilities, Exploits & Attacks
The rising trend of malicious packages in open source ecosystems
Since the beginning of 2023, Snyk has documented around 6800 malicious packages across PyPI and the npm registry, which requires little to no interaction, almost 860 of which were discovered by us.
Rubrik Gets Hit by The GoAnywhere Security Vulnerability: Is Customer Data at Risk?
Rubrik is a security company that specializes in cloud data management services. The company helps store and secure information for customers, and it's vital that it is able to keep that data safe. This is why hearing about a possible cyber-attack on the company is alarming. Rubrik was hit by the same GoAnywhere security vulnerability that dozens of other companies suffered from.
SharePoint Security: 8 Most Common Vulnerabilities
Once written off as a failed CMS incapable of generating a significant user base, Microsoft’s SharePoint has continually defied expectations to become one of the most widely-used ECM and Collaboration products ever. It caters to over 200 million users and 250,000 organizations, including 85% of Fortune 500 companies. SharePoint is a user-friendly intranet portal and provides a consolidated center for document sharing, tracking, and overall project management.
Penetration Testing vs Vulnerability Scanning: What's the Difference?
Penetration Testing (also known as pentesting or ethical hacking) is a simulation of an attack on a computer system, network, or web application to identify potential security vulnerabilities and gauge the effectiveness of existing security measures. These are typically performed by cybersecurity professionals with specialised knowledge and experience in identifying and exploiting system vulnerabilities.
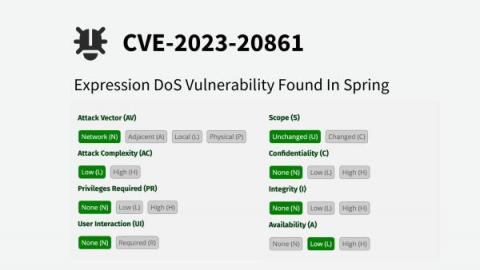
Expression DoS Vulnerability Found in Spring - CVE-2023-20861
Coffee Talk with SURGe: Oakland Ransomware Attack, BreachForums, Acropalypse Vulnerability, GPT-4
Save time fixing security vulnerabilities much earlier in your SDLC
Are you or your development team tired of using application security tools that generate countless results, making it difficult to identify which vulnerabilities pose actual risks? Do you struggle with inefficient or incorrect prioritization due to a lack of context? What adds insult to injury is that traditional CVSS scoring methods ignore critical details like software configurations and security mechanisms.