Critical Requirements for Mobile Security
0:00 Opening
6:06 What is Zero Trust?
11:48 Zero Trust workforce on mobile devices
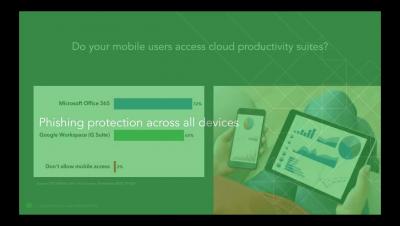
14:57 Enabling Phishing protection on mobile
26:10 Vulnerability management for devices and applications
33:05 Ability to hunt for threats on mobile
43:45 Critical capabilities for comprhensive security
45:20 Q&A