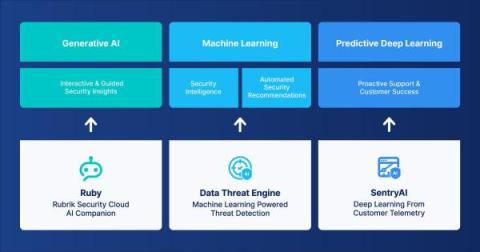
Announcing Ruby - your new Generative AI companion for Data Security
Say hello to Ruby, your new Generative AI companion for the Rubrik Security Cloud. Ruby is designed to simplify and automate cyber detection and recovery, something that IT and Security teams struggle with as cyber incidents are getting wildly frequent and the attacks are evolving quickly. A study by Rubrik Zero Labs revealed that 99% of IT and Security leaders were made aware of at least one incident, on average of once per week, in 2022.