Why outdated access control is putting your data at risk
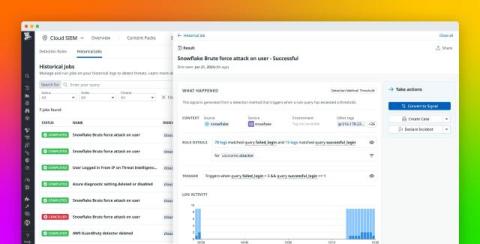
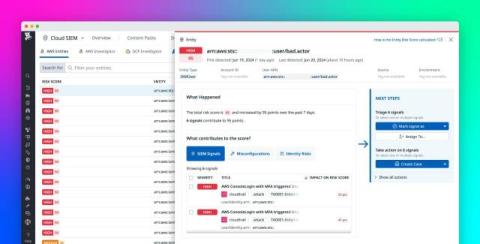
Imagine this: you wake up to a notification – your company has suffered a data breach. Fear sets in as you think about what this means: customer data exposed, your company’s reputation damaged, and big fines on the horizon. In today’s digital landscape, this scenario is too common. Organizations worldwide face penalties for non-compliance with regulations, such as fines of up to $50,000 per incident for violating HIPAA.