Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
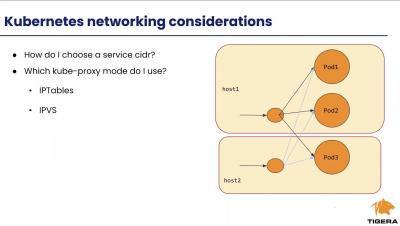
Deploying Calico in Your On-prem Kubernetes Cluster: Networking and Security Considerations
CI/CD With Veracode Docker Images
On November 19, Veracode published new, official Docker images for use in continuous integration pipelines. The images, which provide access to Pipeline Scan, Policy (or Sandbox) scans, and the ability to access Veracode APIs via the Java API Wrapper or via HTTPie with the Veracode API Signing tool, make it easy to include the current version of Veracode tools in your automation workflow.
Three Key Takeaways From Our 'Security in Motion' Summit
2020 has been a challenging year. Organizations had to quickly figure out how to secure employees and mobile endpoints working outside their existing perimeter-based controls. To take a step back, 2020 isn’t an anomaly. This shift to mobile-first was happening well before the pandemic.
Ignyte Assurance Platform Achieves ISO 27001 Certification
December 1, 2020 Miamisburg, OH – Ignyte Assurance Platform, the integrated cyber risk assurance company, announced it has achieved ISO/IEC 27001:2013 certification, recognizing its commitment to providing customers with the highest level of information security management. Following an extensive audit process, the certification was issued by an ANAB and UKAS Accredited Certification Body based in the United States.
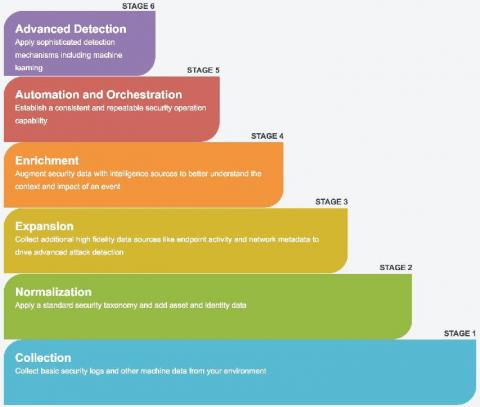
The Third Critical Step to Building the Modern SOC
The new Devo eBook, Building the Modern SOC, presents four evolutionary steps for creating a highly automated and efficient security operations center (SOC) that empowers analysts. This is the third in a series of posts highlighting the most important elements of the four steps. Previous posts covered Step 1, establishing a foundation of centralized, scalable visibility, and Step 2, extracting intelligent insights from your data.
Something Else To Be Thankful For: Splunk Security Essentials 3.2.2
Well, it’s been a while since you read a blog dedicated to the latest release – okay, the latest several releases – of Splunk Security Essentials (SSE). We have been busy behind the scenes, however, so let’s catch you up on SSE’s latest features, which include the new version of our content API, and externally with updates from MITRE and the release of ATT&CK v7.2 (with Sub-Techniques) and ATT&CK v8.
How to secure a Kubernetes cluster
More and more organizations are adopting Kubernetes, but they’re encountering security challenges along the way. In the fall 2020 edition of its “State of Container and Kubernetes Security” report, for instance, StackRox found that nearly 91% of surveyed organizations had adopted Kubernetes, with a majority (75%) of participants revealing that they had deployed the container orchestration platform into their production environments.
IcedID Stealer Man-in-the-browser Banking Trojan
IcedID stealer (Also known as BokBot) was first discovered at the end of 2017, believed to be a resurgence of the NeverQuest banking Trojan. It is a modular banking trojan that uses man-in-the-browser (MitB) attacks to steal banking credentials, payment card information and other financial data. The stealer possesses relatively sophisticated functionality and capabilities such as web injects, a large remote access trojan (RAT) arsenal and a VNC module for remote control.
Calligo acquires Network Integrity Services!
Today Calligo announces it has completed its fourth acquisition of 2020 – and ninth in three years – with the purchase of Network Integrity Services, a UK-wide IT managed services provider specialising in managed IT, cloud and security services with locations in Manchester, Birmingham, Leicester and Hemel Hempstead.