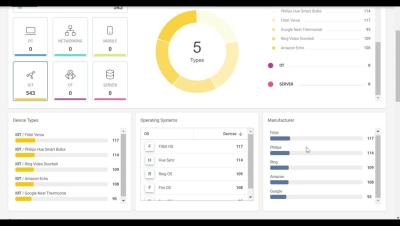
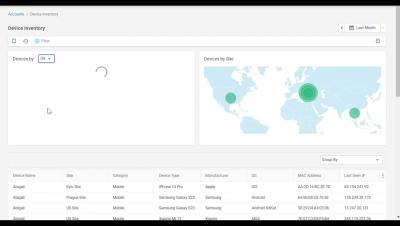
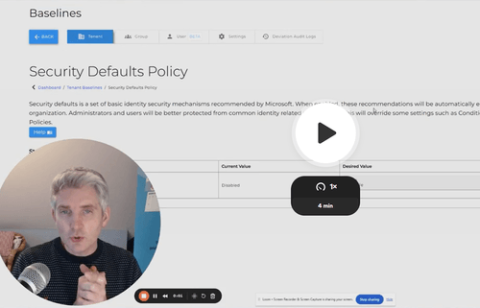
Part of the AWS EDP program? Burn down your commit with 11:11 Systems.
If you’re part of Amazon Web Services Enterprise Discount Program (AWS EDP), we can help you make the most of your EDP commitment. That’s because you can burn down some of the amount you’ve committed to spend by leveraging 11:11 solutions and services.