Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Using Open Policy Agent to safeguard Kubernetes
Open Policy Agent addresses Kubernetes authorization challenges with a full toolkit for integrating declarative policies into any number of application and infrastructure components. As more and more organizations move containerized applications into production, Kubernetes has become the de facto approach for managing those applications in private, public and hybrid cloud settings.
Image scanning for Google Cloud Build
In this article, you will learn how to add inline image scanning to a Google Cloud Build pipeline using the Sysdig Secure DevOps platform. We will show you how to create a basic workflow to build your container image, scan the image, and push it to a registry. We will also customize scanning policies to stop the build if a high-risk vulnerability is detected.
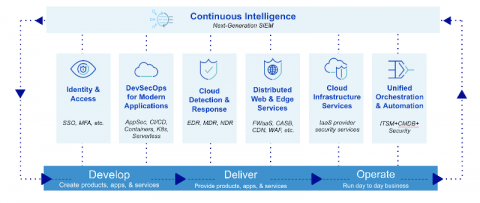
A New Framework for Modern Security
It's All About Access: Remote Access Statistics for Public Cloud Workloads
“The more things change, the more they stay the same.“ In the recent Equinix breach in September 2020, 74 RDP servers were exposed to the Internet. Any publicly exposed ports are a risk but remote access protocols such as RDP have had their share of critical vulnerabilities (e.g., BlueKeep in 2019).
Calico and K8s Network Policies - An Overview and Comparison
How Your Business Can Benefit From Card Issuing APIs
FinTech isn't new, but the reach of its usefulness continues to spread into unexpected areas. One such area is card issuing. Card issuing is the ability of financial institutions to issue debit or credit cards—either physical or virtual. This might not seem like much, but when combined with new business needs and consumer trends we start to see interesting use cases crop up.
The BSIMM: Five key steps to a better software security initiative
If you care about software security—and you should, since to be in business today means that no matter what you do or produce, you’re also a software company—you should be interested in the Building Security In Maturity Model (BSIMM). It can serve as a roadmap to better security.
Veracode Streamlines AppSec Workflows for Developerswith New GitHub Action
Insider threats: What are they and how to prevent them
Companies need to establish a secure system to avoid insider threats and other online issues that could destroy a business. There are different online threats that businesses face every day. The most common of which is phishing attacks were the victim accidentally clicks on an unsafe link and log in. Other commonly known threats to businesses are malware, ransomware, weak passwords, and insider threats. Most of these online attacks are due to what is known as insider threats.