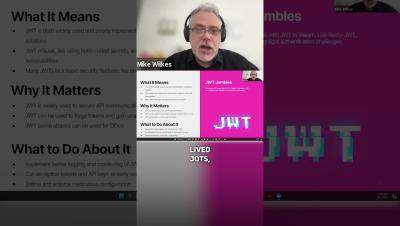
Why Long-Lived JWT Tokens Are a Time Bomb for API Security ? #jwt #api #apisecurity #apiattacks
Long-lived JSON Web Tokens (JWT) can pose serious security risks if not properly managed. Learn how these tokens can be exploited and why regular security reviews and Canary tokens are essential to protecting your APIs.