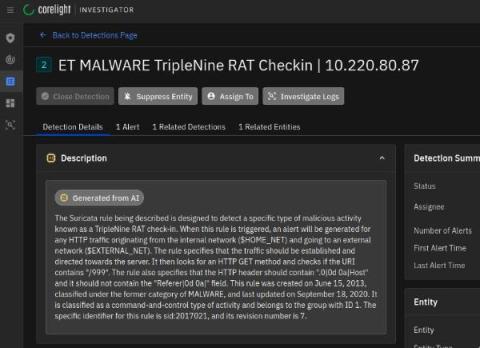
Turning the tables on the infiltrator
What happens at the point in time when an organization’s information security is compromised? This blog explores an important paradigm shift that occurs at the very moment of compromise and that can be leveraged to turn the tables on the attackers.