Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Networks
ObjectFlow APIs: How to authorize your endpoints in seconds
One SIEM is not enough?
The idea behind the SIEM (and now XDR!) technologies was to provide a single engine at the heart of the SOC, aggregating data, enabling analytics and powering workflow automation. The SIEM would act as one place to train analysts and integrate a range of complementary technologies and processes. Given the efficiency that comes from centralization, I was surprised to hear that a growing number of defenders are actually using two SIEMs. Why is that?
Monitoring Cyber Threats Tied to the Russia-Ukraine Conflict
Beyond the disturbing images of the invasion of Ukraine that began February 24 are the invisible cyberattacks that preceded it and continue to be waged on Ukraine by Russian state-sponsored and other threat actors, which also threaten the West. Vedere Labs, Forescout’s threat intelligence and research team, is closely monitoring the evolution of cyber activities connected to the Russian-Ukrainian conflict.
Reverse Proxy Vs. Load Balancer
A reverse proxy server (or reverse proxy) facilitates a user’s requests to a web server/application server and the server’s response. A load balancer receives user requests, distributes them accordingly among a group of servers, then forwards each server response to its respective user. From the brief definitions above, it’s clear that reverse proxies and load balancers have some overlapping functionalities.
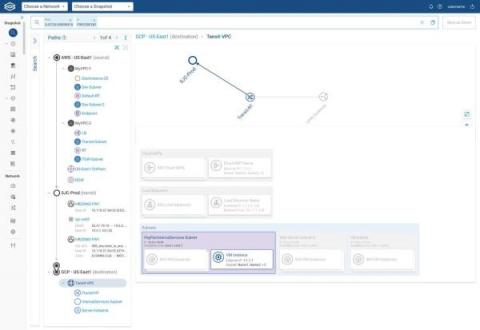
View All Your Clouds in a Single Pane of Glass
If your enterprise is like most of Forward Networks’ customers, then your IT shop oversees a sizable cloud estate. You probably have hundreds of accounts, projects, or subscriptions across different cloud vendors. There are tons of related objects too — virtual machines, firewalls, transit gateways, subnets, and more. And cloud-native apps? Maybe you hundreds of those in use or development as well.
EndaceProbe Release Changes the Game for Network Forensics
Webinar: The Importance of Firewall in a Unified Security Platform - 15 Feb 2022
Cybersecurity Asset Management: Know What's on Your Network
Guessing how many marbles are in a jar is either a fun carnival game (pick the average based on the wisdom of the crowd) or a math problem involving orb volume, cylinder volume and the estimated space between marbles. You can also just count the marbles. Unfortunately, when it comes to identifying the number of devices connected to your network, none of these approaches works – although quasi-manual counting remains all too common.