Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Networks
BOD 23-01 April 3, 2023, Deadline for Federal Agencies: Are You Ready?
On October 3, 2022 the Cybersecurity and Infrastructure Security Agency (CISA) issued Binding Operational Directive 23-01 – Improving Asset Visibility and Vulnerability Detection on Federal Networks, a compulsory order intended to “make measurable progress toward enhancing visibility into agency assets and associated vulnerabilities.” BOD 23-01 mandates that Federal Civilian Executive Branch (FEEB) agencies complete a series of required actions within six months, or by April 3, 2023.
Ensure a secure IT environment with integrated network vulnerability management
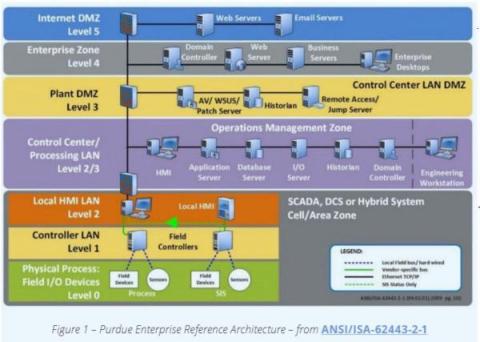
Deep Lateral Movement in OT Networks: When Is a Perimeter Not a Perimeter?
Forescout’s Vedere Labs latest research report is the first systematic study into deep lateral movement: how advanced adversaries can move laterally among devices at the controller level – also known as Purdue level 1 or L1 – of OT networks.
Understanding Direct Cloud Connectivity: Jargon and Benefits
From Noise to Signal: Enrichment and Routing with Corelight, Cribl, and Elastic
How to Secure Your Home WiFi Network
Wireless devices on your home networks can include everything from PCs, phones and tablets to IP cameras, voice assistants, smart TVs and connected appliances. Simple precautions you take to secure your home WiFi network will help prevent cybercriminals from accessing your devices and stealing your data. You can secure your WiFi network by creating a separate guest WiFi network, turning on your router’s encryption, using a VPN for further protection and more.
What's the Difference Between HTTP vs HTTPS?
One of the biggest indicators of a suspicious or unsecured website is whether or not the site is HTTPS-secured. In many cases, spoofed, phishing, malicious, or typosquatted websites use HTTP instead of HTTPS, which has encryption and verification protocols built in to ensure safe data transmission between servers and browsers. The main difference between HTTPS and HTTP is that HTTPS establishes a secure internet connection via encryption, whereas HTTP does not.
Startup and Stability, Surprisingly now in the Same Sentence?
These are uncertain times in tech. If you’re at one of the many companies in the news recently, think back to why you joined. Was it the people? The tech? Or maybe… the perception of a rock-solid, not-going-anywhere, totally-guaranteed position? Things have changed lately.