Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Networks
Fortify Your SD-WAN With SSE Integration
Many of today’s security tools are built to secure cloud services. But we need to keep in mind that many organizations still require configurations that don’t have direct connection to the cloud. Organizations that have numerous branch locations — like convenience stores, school districts and banks — often use a software-defined wide area network, or SD-WAN.
Cyber Skills Shortage? The Time for Security Automation Is Now
Many industries are affected by skills gaps, but according to Cybersecurity Ventures, the shortage within the IT/cybersecurity sector is nearly unmatched: Over an eight-year period, the number of unfilled cybersecurity jobs increased from one million positions in 2013 to 3.5 million in 2021.
SANS 2022 Report Moving to a State of Zero Trust
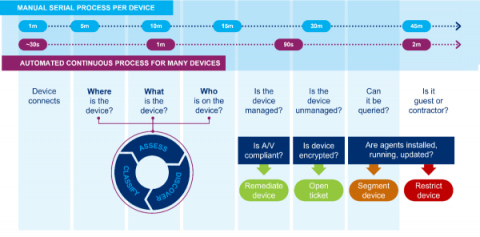
Why application-centric security is crucial for your organization
How to Benchmark Your Threat Hunting Readiness and Prepare for the Next Step
Network Forensics & Incident Response with Open Source Tools
Ransomware in Healthcare: The NHS Example and What the Future Holds
On August 4, 2022, Advanced – a major software provider for the UK’s National Health System (NHS) and other healthcare customers – suffered a ransomware attack from a group that is still unknown to the public. The attack disrupted NHS services including ambulance dispatch, appointment bookings, patient referrals and emergency prescriptions.
What to Do When Ransomware Meets the Internet of Medical Things
Vedere Labs recently developed a proof-of-concept (PoC) ransomware for IoT (R4IoT) using as an example attack scenario a hospital network containing IoT devices such as IP cameras, IT workstations and OT in the form of building automation controllers.