Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Logging
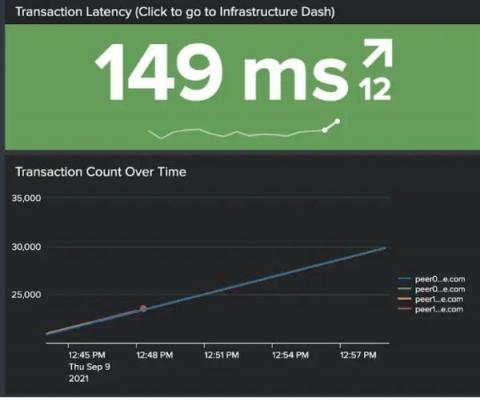
Hyperledger Fabric Security Monitoring with Splunk
In this post, we demonstrate how to set up effective security monitoring of your Hyperledger Fabric infrastructure. We identify some common threats, recognize key data sources to monitor, and walk through using Splunk to ingest and visualize your data. This post follows Introducing Splunk App for Hyperledger Fabric and highlights the use of the app for security monitoring of blockchain infrastructure. We will address smart contract/chaincode security & monitoring in a follow-up post.
Understanding business and security risk
Even if an organization has developed a governance team, aligning integration decisions with business needs must be incorporated into the zero trust architecture. The company’s business model drives the applications chosen. The senior leadership team needs someone who can translate technology risks and apply them to business risks. For example, security might be an organization’s differentiator.
Configuring an Output with LimaCharlie
Forwarding Access Logs using FluentD
https://goteleport.com/docs/setup/guides/fluentd/
0:00 Intro
0:35 Forwarding events with Fluentd
6:54 Setting up ElasticSearch
11:02 Setting up FluentD
14:02 Viewing events in LogStash
Searching data - Devo query lookups
Congress Should Support Cybersecurity Through Log Standardization Funding
In late August, the Office of Management and Budget (OMB) issued an implementation memo regarding Section 8 of the administration’s cybersecurity executive order, which focused on security through data log management.
Devo's Latest Release Empowers Analysts to Discover Threats Faster and More Accurately
Over the past 12 months, the cyberthreat landscape has become much more tumultuous. A data breach analysis from the Identity Theft Resource Center (ITRC) found that the number of data breaches publicly reported so far this year has surpassed the total for 2020. That’s alarming. To combat this constant barrage of cyberattacks, you must equip your security team with the tools they need to match the pace of today’s data growth and cybercriminals’ relentlessness.
Top seven logging and monitoring best practices
Need to build a logging and monitoring solution and unsure where to begin? Get started with our logging and monitoring best practices guide. By: Nivedita Murthy, senior security consultant, and Ashutosh Rana, senior security consultant, at Synopsys.
Small IT Teams with Big Security Problems
Not every organization is - or even wants to be - a Fortune 500. Unfortunately, cybercriminals don’t care how big your company is. In fact, they often look to target small and midsize businesses (SMBs) knowing that they might have fewer security resources. You have the same problems that the big companies have, but you also have less money and people. Using centralized log management can give you the security solution you need, at a price you can afford.