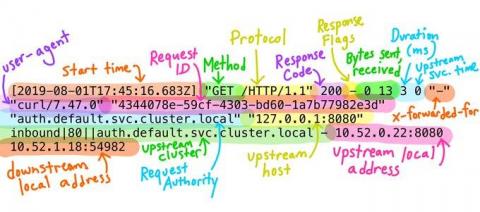
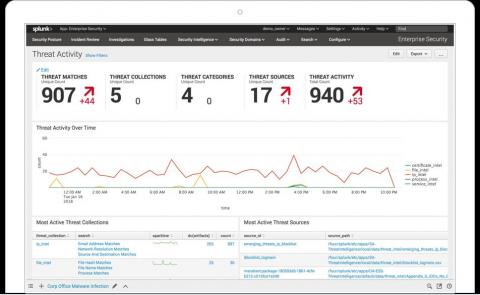
Best Practices for Delivering a Business-Driven Security Posture
The main focus for cybersecurity teams — moving beyond compliance — is to deliver the level of security required to manage the likelihood of a breach and the potential impact to the business. This is more effective than simply focusing on the cost of delivering security services.