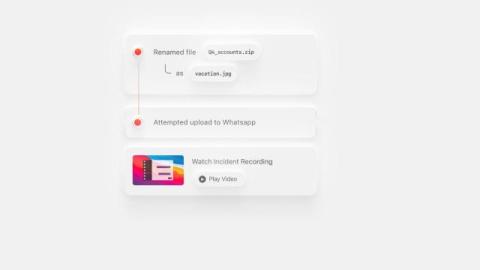
Why Therapists need Data Protection and Cybersecurity
Did you know the New-Age Therapeutic sector is unregulated? If that surprises you, then you’re not alone. I was a little surprised, too. Yes, there are various professional bodies a practitioner can join, and there are courses they can attend, but they aren’t forced to.