Recapping the Splunk for CMMC Solution Launch
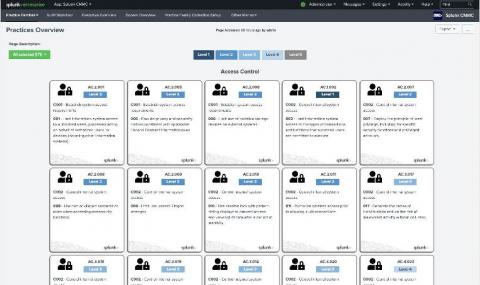
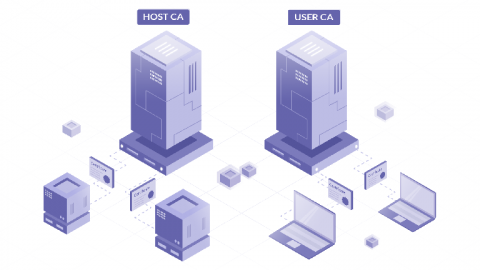
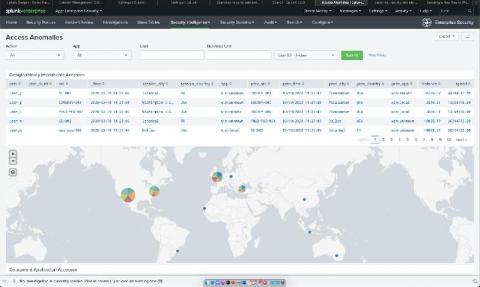
On Wednesday, March 25th, we launched our Splunk for CMMC Solution with a webinar presentation to a diverse set of defense industrial base (DIB) participants and partners. As I discussed during the launch event, the Splunk for CMMC Solution provides significant out-of-the-box capabilities to accelerate organizations’ journeys to meet, monitor, track, and mature the cybersecurity practices required by the Cybersecurity Maturity Model Certification (CMMC).