SolarWinds Supply Chain Attack
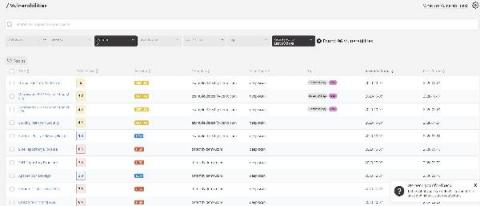
Following the attack on FireEye, the US Department of Homeland Security (DHS) has issued an Emergency Directive (ED) regarding a backdoor being exploited in SolarWinds Orion products, versions 2019.4 through 2020.2.1 (inclusive). Based on file signatures, FireEye considered this campaign to have started around March 2020, potentially affecting up to 18,000 organization worldwide.