Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
SOAR
The latest News and Information on Security Orchestration, Automation and Response.
What is SOAR and how does it improve threat detection and remediation?
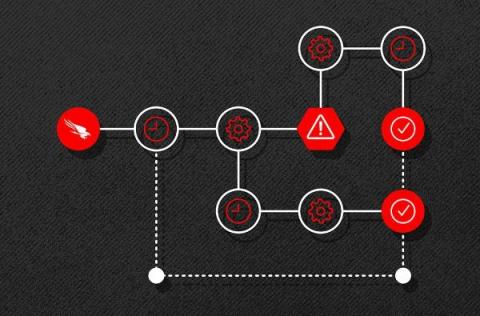
SOAR (Security Orchestration, Automation and Response) refers to the combination of three different technologies: security orchestration and automation, security incident response platforms (SIRP) and threat intelligence platforms (TIP). SOAR technologies allow organisations to collect and aggregate vast amounts of security data and alerts from a multitude of sources.
New CrowdStrike Falcon Fusion Features Refine Workflow Automation for CrowdStrike Customers
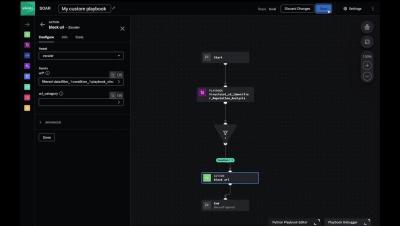
CrowdStrike Falcon® Fusion is a cloud-scale, extensible security orchestration, automation and response (SOAR) framework that’s natively integrated with the CrowdStrike Falcon® platform and available to CrowdStrike customers at no added cost.
Send Your SOAR Events to Splunk
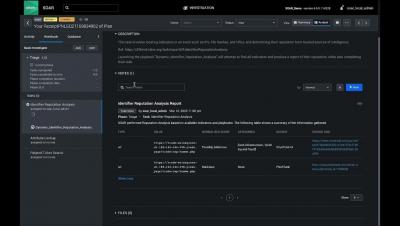
Splunk SOAR Playbooks - Dynamic Identifier Reputation Analysis (Part 1)
Splunk SOAR Playbooks - Dynamic Identifier Reputation Analysis (Part 2)
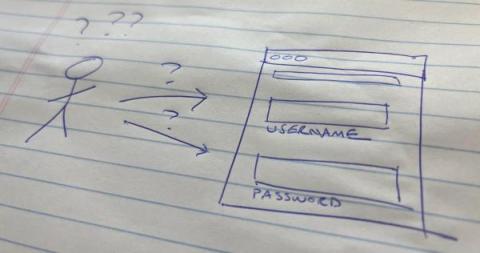
My Username Fields Have Passwords in Them! What Do I Do?
SOAR'ing to Success: How a Leading Software Vendor Monitors FTP Traffic
Software vendors have loads of high-value data they need to protect — from customers’ personally identifiable information to the company’s intellectual property — so a data breach can be catastrophic. There’s a lot on the line if these types of organizations fall victim to a cyberattack, including fines from regulators or damage to their brand and reputation.
Year in review: ManageEngine Log360's analyst recognition from 2022
Cyberattacks have intensified over the last few years as threat actors are always improvising their game plan to carry out new and sophisticated methods. Concepts like Ransomware as a Service have made it easy for small threat groups to leverage weaponized services with devastating results for organizations. This highlights how traditional security systems and approaches are no longer able to keep up with the ever-evolving threat landscape.