Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
SOAR
The latest News and Information on Security Orchestration, Automation and Response.
Automating With Splunk Phantom: How Norlys Does It
Some tasks are better off automated. Paying bills on time? Automated payments. Orchestrating a coordinated response to security alerts and triaging security events? There’s Splunk Phantom for that. Monotonous tasks, in our work and personal lives, should and can be automated in order to free up time and energy to focus on the things that matter.
A Path to Proactive Security Through Automation
The sheer number of cyberattacks launched against organizations every year is massive and growing. If you’re a security analyst working in a SOC or security team, tasked with defending your organization, that means you’re getting bombarded by many more attacks than the recorded numbers above would suggest. These attacks translate into security alerts — fired from your various security tools — that you must investigate and resolve.
Next Level Automation: What's New with Splunk Phantom
Splunk Phantom 4.10 introduced many new enhancements, including the ability to develop playbooks in Python 3. In fact, Python 3 is now the default for Splunk Phantom playbooks. In doing so, we needed to create two different “playbook runners” to ensure we could continue to support playbooks written in Python 2.7 while also supporting Python 3.
Splunk SOAR Playbooks: Finding and Disabling Inactive Users on AWS
Every organization that uses AWS has a set of user accounts that grant access to resources and data. The Identity and Access Management (IAM) service is the part of AWS that keeps track of all the users, groups, roles and policies that provide that access. Because it controls permissions for all other services, IAM is probably the single most important service in AWS to focus on from a security perspective.
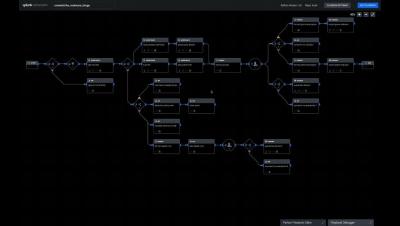
Splunk SOAR Playbooks - AWS IAM Find and Disable Inactive Users
Automation Made Easy: What's New with Splunk Phantom
The Splunk Security Team is excited to share some of the new and enhanced capabilities of Splunk Phantom, Splunk’s security orchestration, automation and response (SOAR) technology. Phantom’s latest update (v4.10) makes automation implementation, operation and scaling easier than ever for your security team.
What is Security Orchestration Automation and Response?
With the face of cyberthreats in a constant state of flux, it’s nearly impossible for IT and Security teams to manually secure their countless systems, applications, services, and devices, as well as respond to potential and active cyberattacks that manage to flourish despite best efforts.
Denmark's Largest Utility Company Accelerates Incident Response
As Denmark’s largest power, utility and telecommunications company servicing 1.5 million customers, Norlys understands the need for fast response to security alerts. When the company first started, the Norlys security team built their own log analytics and incident response capabilities from the ground up. This homegrown approach presented challenges, including manual workflows, too many repetitive tasks and difficult-to-maintain processes.