Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Malware
How Rubrik Supports NASCIO 2023 Priorities
The annual State CIO Top 10 priorities list issued by the National Association of State Chief Information Officers shows that while the technology initiatives remain relatively unchanged, there is a slight shuffle around priorities. Cybersecurity continues to take the number one spot and will likely be the case for years to come, given the increase in ransomware attacks across industries and organizations of all sizes.
Disabling Backups! - A Ransomware Story
Ransomware Report 2023: Targets, Motives, and Trends
Our annual Ransomware Report shares the latest trends and developments of the most active threat groups, and their victims to help businesses better protect themselves.
Active ESXiArgs Ransomware Campaign Targeting ESXi Servers Worldwide
Hive Shutdown Incident
Nevada Ransomware Campaign
Hive Ransomware Technical Analysis and Initial Access Discovery
Hive has been seized by law enforcement, but were likely to still see these initial access methods and tactics used across other threat actor groups.
4 Strategies to Stay Secure in a Connected World
Cybersecurity is a complex term, it’s become all-encompassing and constantly evolving to include new and emerging technologies, attacks, actors, and a myriad of other points. What this means for organizations large, medium, and small is that each must have a cybersecurity plan in place. An interesting point, however, is despite the mindshare cybersecurity now enjoys, the industry itself is still in its relative infancy.
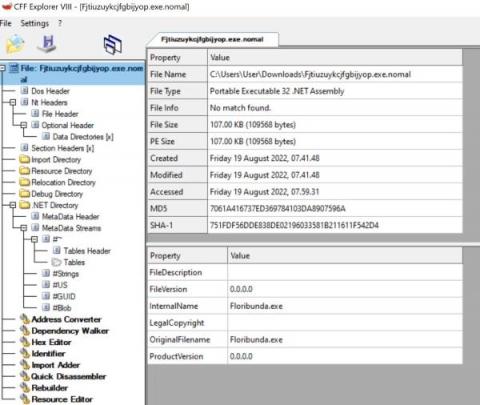
Redline Infostealer Analysis (Part 2)
Redline infostealer gathers information and steals high value data from an infected machine. The Redline infostealer is considered one of the most dangerous malware currently being used in the wild and has been used in countless trojanized software, applications, games and cracked software. In addition to data exfiltration, Redline also has the capability to connect to a command and control (C2) server to download, upload files as well as perform remote commands.