Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest Videos
Custom Frameworks
TrustCloud supports several standards and frameworks out of the box, including SOC 2, CMMC, and ISO 9001, to name a few. The best part is that TrustCloud is constantly adding new frameworks to expand the TrustCloud Common Control Framework (TCCCF). Organizations, regulations, and business needs are constantly evolving, and therefore, you might need certain frameworks that are currently not supported by the TrustCloud platform. To enable you to meet your ever-evolving framework needs, TrustCloud now offers the flexibility of creating your own custom frameworks and standards.
JUMPSEC A red teamer's forecast - Cloudy with a chance of hacks
A red teamer’s forecast – Cloudy with a chance of hacks Our adversarial simulation team will outline how attackers exploit cloud infrastructure and offer strategies to counter their efforts. Key insights involve recognising significant security risks in cloud adoption, including emerging attack vectors, comprehending hacker tactics in cloud settings, and swiftly implementing effective measures to safeguard cloud environments.
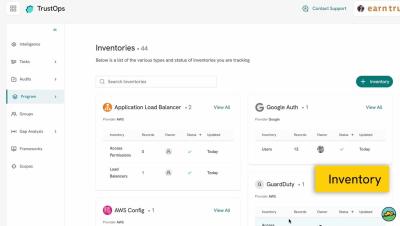
Inventory - What is it? How can you use it as evidence?
An inventory is a specific list of data that is gathered to provide information about a certain part of the business. The inventory is inspected by an automated test or by a human to determine if one or more controls are satisfied and to analyze the results of the inventory. Examples of inventories are users, security incidents, devices, servers, databases, logs, etc.
See Falcon Fusion in Action
Breach containment is a race against time. Falcon Fusion, integrated within the CrowdStrike Falcon Platform, harnesses AI and automation to expedite incident detection and response. Experience how Falcon Fusion streamlines security workflows, enabling teams to take down threats 108 days quicker on average, providing a swift and strategic defense that keeps adversaries at bay. CrowdStrike Falcon Fusion SOAR.
MSASE License Pre-Staging and Pre-Configuration
Through the MSASE Partner Platform, Cato enables partners to do pre-configuration and feature staging prior to a customer account going live. This enables partners to immediately start realizing revenue, without any days lost in staging or pre-configuration. Additionally, customers get the benefit of immediate "day-zero" SASE feature capabilities.
Octiga 3 minute demonstration (website)
How Octiga enables MSPs to deliver effective and efficient multi-tenant Microsoft 365 security for their clients.
Creating Users Manually | JumpCloud University Tutorial (2024)
In this tutorial, we will go over how to create a user in JumpCloud manually. This method can be used when you need to add a single user. To discover more resources checkout JumpCloud University where you’ll find courses, tutorial videos, engaging guided simulations, and end user content.
How to Set Up Real-Time Data Replication for VMware VMs with NAKIVO Backup & Replication
The Real-Time Data Replication for VMware functionality in NAKIVO Backup & Replication allows you to create real-time replicas of VMware VMs, continuously updated with source VM changes. Follow the steps in this video to learn how to deploy a target Transporter, install the I/O Filter and Journal Service, and create your first real-time replication for VMware vSphere with NAKIVO Backup & Replication.
Building a Human-Centric Vulnerability Management Program
Steve Carter, CEO and co-founder of Nucleus Security, and Dr. Nikki Robinson, Security Architect at IBM, discuss the importance of the people side of vulnerability management. They explore challenges such as context switching, long mean time to remediation, and the impact of communication on vulnerability management programs. The conversation includes practical advice on incorporating human factors into cybersecurity practices, how to improve communication and collaboration among teams, and why understanding human factors is crucial for effective vulnerability management.