Hardening Infrastructure Security Against SSO Identity Provider Compromise
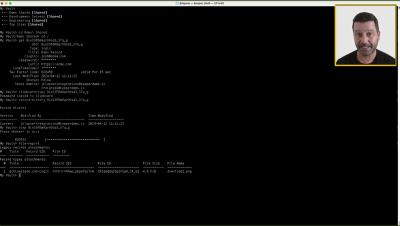
In an era where Identity Providers (IdPs) have become prime targets for cyber attackers, relying solely on single sign-on (SSO) authentication can leave organizations vulnerable to various sophisticated threats such as social engineering, credential stuffing, and session hijacking. Join us for an in-depth webinar to explore how Teleport is redefining infrastructure security strategies that protect infrastructure even in the event of identity provider compromise.