Edit and Assign Security Labs Roles to Users
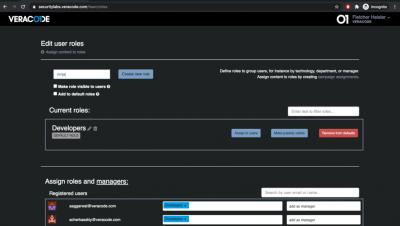
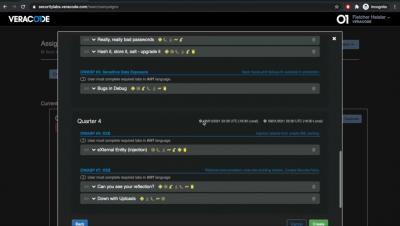
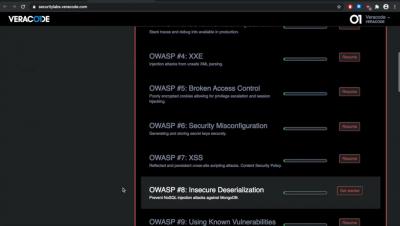
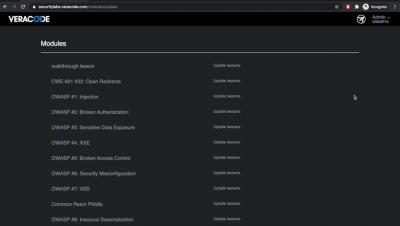
In this video you will learn how to edit roles, assign roles to users, and create managers for those roles. Veracode Security Labs provides interactive training labs that give developers practical security knowledge.