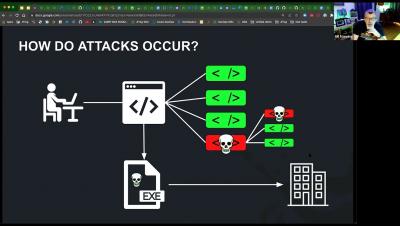
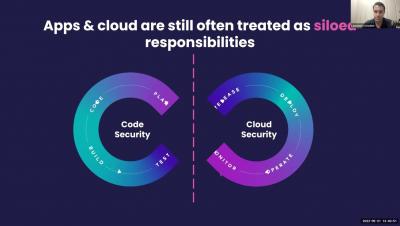
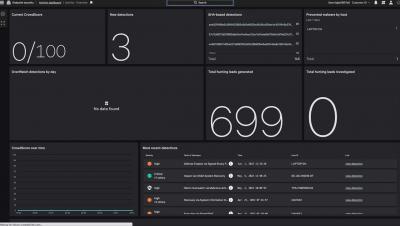
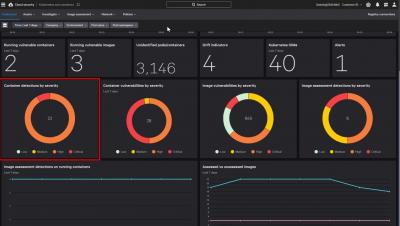
Zero Trust goes beyond standard security
Zero Trust is a modern, strategic approach to cybersecurity that secures organizations by eliminating implicit trust and continuously validating all interactions and experiences. Zero Trust moves cyber defenses from static, network-based perimeters to focus on users, assets, applications and resources without any implicit trust to enhance posture and reduce risk. At its core, Zero Trust is a perimeterless security approach.