Cyber Risk Progression Feature Empowers CISOs to Highlight Success Over Time
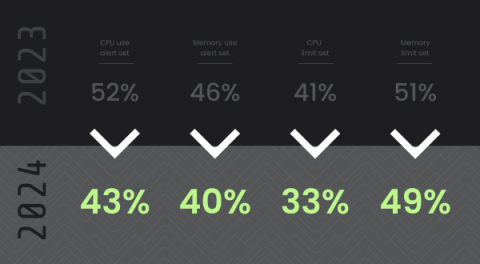
For chief information security officers (CISOs), understanding how their organization's unique cyber risk landscape has evolved is paramount. Chronological analysis not only enables risk trends to emerge with more clarity but also provides the essential context required for more informed decision-making.