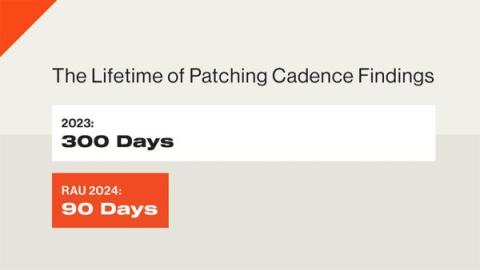
What is Policy Orchestration?
As an organization’s data volume grows, so does the need to manage its access and governance consistently and securely. The proliferation of vast and siloed data spread across diverse applications, multi-cloud and hybrid environments, and formats over the last few decades has made it difficult to control data access and governance. In order for structured data to be effectively utilized, it needs to be combined and enhanced in a way that supports both operational and analytical tasks.