Java, JavaScript, .NET: Which Has the Riskiest Security Debt?
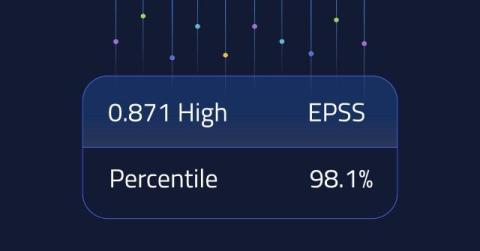
In the realm of secure software development, managing security debt is crucial. The following data highlights a concerning trend in the accumulation of critical security debt, particularly in the popular programming languages of Java, JavaScript, and.NET. Let’s dive into this new research and explore options for managing the prioritization dilemma we’re seeing.