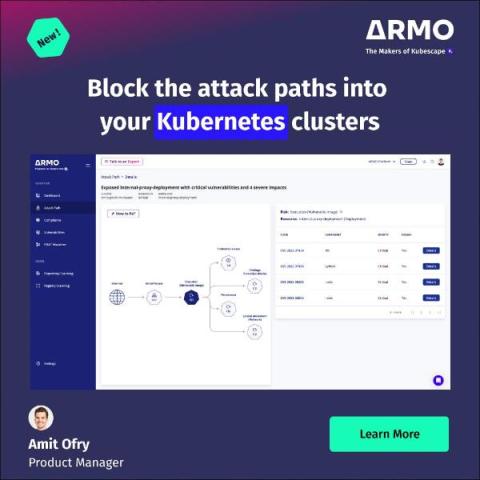
Top Challenges in Implementing SIEM Solutions
Security Information and Event Management (SIEM) systems are the modern guardian angels of cybersecurity, offering robust threat detection, efficient incident response, and compliance tranquility. However, beneath the surface of these promising advantages lie intricate challenges. In this blog post, we delve deep into SIEM implementation challenges. But before diving in, let's first understand what SIEM entails.