Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Building Security Culture Starts with Building Relationships
Code doesn’t write itself and software doesn’t secure itself, as much as the race is on to make that happen. At the beginning and end of everything in software is people and, importantly, people interacting with each other. Having great tools doesn’t matter if no one uses them, and having great policies doesn’t matter if no one enforces them.
How Loctax uses Aikido Security to get rid of irrelevant security alerts & false positives
MSSP Alert Names CISO Global to 2023 Top 250 Managed Security Services Providers List
Business Email Compromise Attacks (BEC) Keep Growing - Here's How to Increase Your BEC Cybersecurity
This spring, Australian authorities were able to arrest a cybercrime syndicate that had conducted BEC attacks on at least 15 individuals and organizations with stolen profits totaling $1.7 million (USD). If those numbers seem shocking, they’re part of a growing upward trend of BEC attacks that shows no sign of slowing down.
Bah, Humbug! Grinchbots and Freebie Bots Attempt to Ruin Holiday Shopping for Consumers and Retailers
If the holiday classic “How the Grinch Stole Christmas” was remade in 2023, the mean green guy might be played by an Internet bot. Sure, these bots may not come down your chimney and steal a tree or holiday dinner, but threat actors have designed them to help ruin retailer and consumer holiday shopping experiences. Trustwave SpiderLabs exposed how the two primary bot variants, Grinchbots and Freebie Bots, operate in the team's recent report.
DDoS Attack Mitigation Playbook for SOC and DevOps Teams
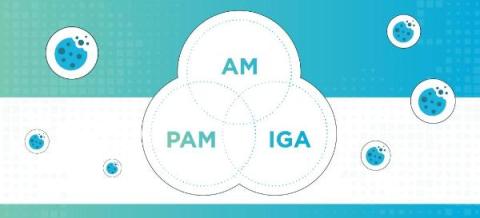
Strengthening Cyber Defenses: The Crucial Role of PAM and IGA Solutions
We recently published a blog titled Defending Your Organization Against Session Cookie Replay Attacks. This blog thoroughly examined the menace of session cookie replay attacks, shedding light on the potential risks and consequences they pose to online security. The post delved into the intricacies of session cookie replay attacks, detailing their working mechanisms and the extensive damage they can inflict and emphasizing the imperative need to comprehend and fortify against such threats.
How Egnyte Migrated Its DNS At Scale With No Service Disruptions
Egnyte, as a custodian of vast volumes of customer data and files, manages billions of files and petabytes of data originating from millions of users. With a system processing over a million API requests per minute, spanning metadata operations and analytical queries, the need to balance throughput and maintain exceptional service quality is paramount.
SMB Protocol Explained: Understanding its Security Risks and Best Practices
Server Message Block (SMB) protocol is a communication protocol that allows users to communicate with remote servers and computers, which they can open, share, edit files, and even share and utilize resources. With the expansion of telecommunications, this protocol has been a prime target for threat actors to gain unauthorized access to sensitive data and devices. In 2017, we introduced 5 general ways to protect your network from SMB risks.