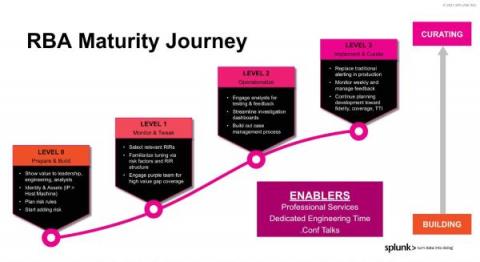
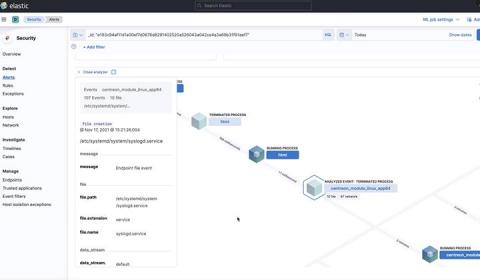
The Linux process and session model as part of security alerting and monitoring
The Linux process model, available within Elastic, allows users to write very targeted alerting rules and gain deeper insight into exactly what is happening on their Linux servers and desktops. In this blog, we will provide background on the Linux process model, a key aspect of how Linux workloads are represented.