Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Convince Your Boss You Need These Managed IT Security Services
Considering managed it security services? It is more important than ever to have a resilient security posture. Hackers are constantly looking for ways to exploit weaknesses in systems, and even a small data breach can have devastating consequences.
Elastic continues to gain momentum in SIEM market
2022 Gartner Magic Quadrant for SIEM: Sumo Logic positioned as a Visionary for the second year in a row
Monitoring Transaction Log Files for PCI compliance
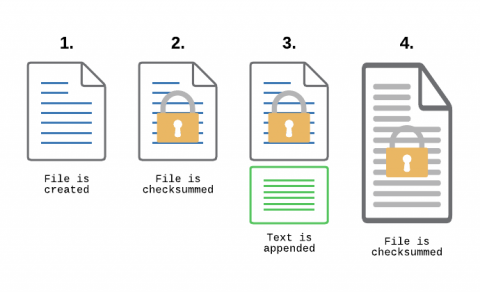
File Integrity Monitoring, aka as FIM, is a must-have feature for anyone in charge of security. With FIM, one can detect when a critical file, such as a file that belongs to the Operating System, or a key configuration file, is changed. In most cases, configuring FIM is straightforward: If the file changes then generate an alert.
Datadog alternatives for cloud security and application monitoring
2022 Devo SOC Performance Report: Familiar Challenges Facing Security Workers
The fourth annual Devo SOC Performance ReportTM shows that issues facing organizations since the start of the global pandemic in early 2020 continue to affect SOC performance, including challenges in hiring and retaining SOC talent. Based on the independent survey of more than 1,000 global cybersecurity professionals commissioned by Devo and conducted in the Summer of 2022, the report examines current SOC trends and challenges. The good news?
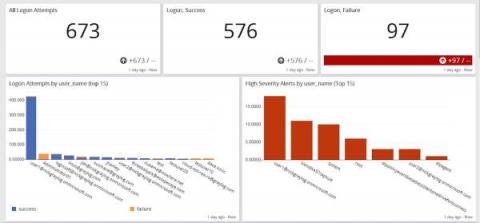
7 key features of SIEM that every enterprise administrator should be aware of
A SIEM solution has become an integral part of an organization’s security arsenal. But organizations often overlook the system’s capabilities, owing to a belief that SIEM functionalities are too complex and the architecture inscrutable. Regrettably, they neglect to meet the requirements of their organization with the features of the product. For instance, an organization that deals with the credit card information of customers needs to comply with the PCI-DSS requirement.