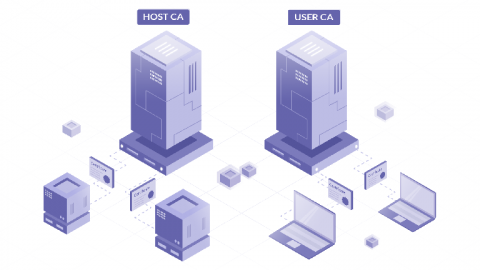
The foundation of a Zero Trust architecture
Organizations have placed a lot of time, effort and capital spend on security initiatives in an effort to prevent security breaches and data loss. Even the most advanced “next generation” application layer firewalls filtering malicious traffic at the network perimeter has only revealed equal if not greater threats within.