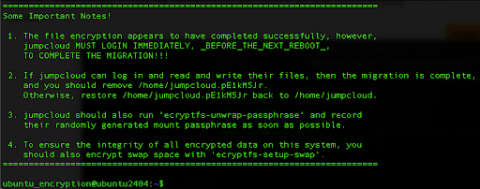
How to Plan an Active Directory Migration
Microsoft’s Active Directory (AD) runs your Windows network and keeps mission-critical legacy apps and workflows running at some organizations. Replacing can be a big commitment and migration planning is an essential step to undertake before kicking off your project. Big commitments are made for very good reasons. Consider that AD has become a top target for cyber attackers and doesn’t meet modern IT requirements.