Fine-tuning Cloud SIEM detections through machine learning
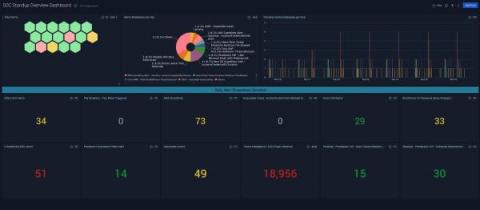
Security engineering teams spend hours every week tuning their security information and event management (SIEM) systems to ensure that they are effective at detecting security threats and minimizing false positives. Such “tuning tax” is common as customers add new SIEM rules to cope with rapidly changing threat landscape and attacker tactics and as their attack surface evolves through automated changes to their application and infrastructure stacks.