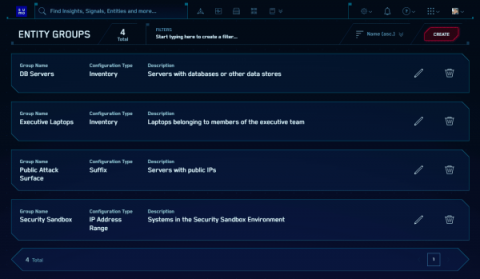
Use new Cloud SIEM Entity Groups to make threat response more efficient
Security analysts and administrators need every advantage to keep up with prioritizing and investigating alerts. A SIEM (security information and event management) solution helps uncover threats, but it takes a lot of time assigning and updating tags, criticality, and signal suppression. Sometimes users opt to skip the step altogether, especially if there are a lot of entities to add or update at once. Other times, they introduce errors during this manual step.