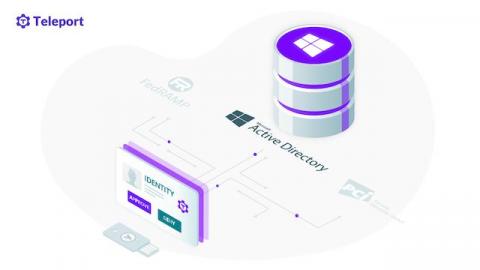
BeyondCorp, Federal Zero Trust Architecture Strategy and Teleport
"Crunchy on the outside, chewy in the middle". That's how Google described its perimeter-based security targeted high-profile companies such as Google, Adobe, Akamai, Rackspace, etc., with said primary reason of modifying the source codes. In response, Google initiated a perimeter-less and trustless access control system now popularly known as BeyondCorp. BeyondCorp comes from a realization that VPN perimeter network security is obsolete.