FBI Notice Underscores Cyberthreats Posed by Medical Devices and IoMT - Risk Management Can Help
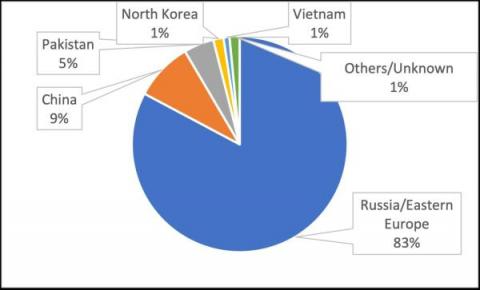
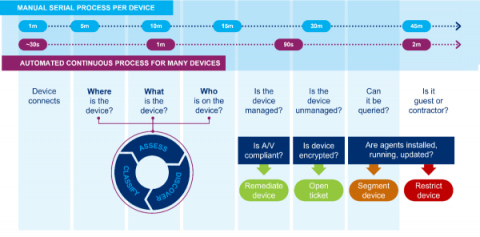
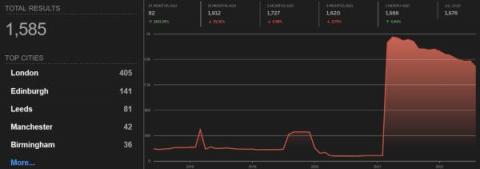
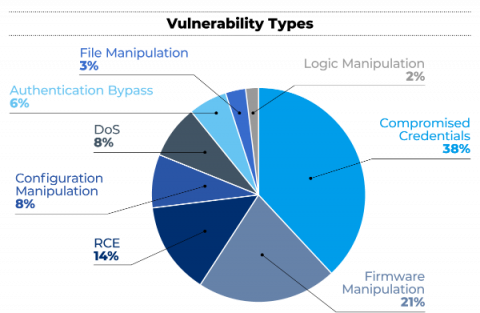
On September 12, the FBI released a private industry notification entitled “Unpatched and Outdated Medical Devices Provide Cyber Attack Opportunities.” The notification underscores how a growing number of vulnerabilities in medical devices and Internet of Medical Things (IoMT) assets can be exploited by threat actors to “impact healthcare facilities’ operational functions, patient safety, data confidentiality and data integrity.”