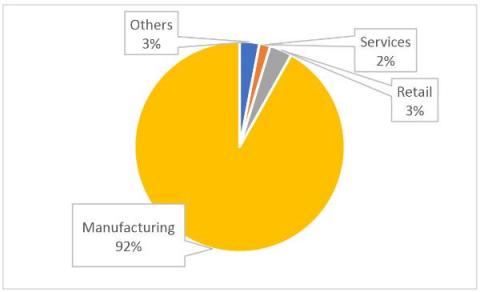
What Project Memoria Foretold about TCP/IP Security and Supply Chain Vulnerabilities
Project Memoria was the largest study about the security of TCP/IP stacks, conducted by Vedere Labs and partners in the cybersecurity industry. It started from a collaboration with JSOF to understand the impact of Ripple20 and led to the discovery of almost 100 vulnerabilities in 14 TCP/IP stacks, divided into five phases: AMNESIA:33, NUMBER:JACK, NAME:WRECK, INFRA:HALT and NUCLEUS:13.