The Fundamentals of Network Access Management
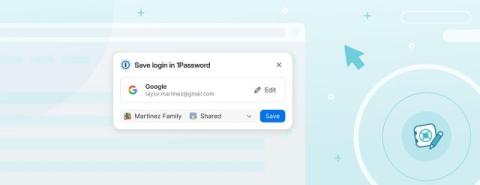
With cyber threats constantly evolving, securing your network is more than just strong passwords or firewalls—it’s ensuring that the right people have access to the right resources at the right times. Understanding and implementing effective network access management is the cornerstone of protecting valuable data and maintaining operational efficiency.